If you came to this page without reading the introduction please go back for a brief introduction, the advantages of this method and how it works.
Use this setup if you already have a DD-WRT router in your network and plan to configure Ace VPN on it for entire house protection.
Requirements
- Ace Premium SSL VPN account or Ace Ultimate SSL VPN account
- Router running DD-WRT firmware (Mega or VPN build).
- If you do not have a router flashed with DD-WRT. Please flash it first and continue with the instructions. Check if your router is supported
DD-WRT Demo
Check out the demo of DD-WRT V24 SP2 to get a fair idea of the features available with dd-wrt flashed router.
Warning
- This tutorial requires basic knowledge about routers and networks. If you have no prior knowledge we suggest you to familiarize about routers and networks before you continue
- Flashing third party firmware can void your routers warranty
- AceVPN.com is not responsible for any damage to the hardware, systems, or personal injury if you do attempt this!
- Only attempt if you are confident in your skills!
Assumptions
- You have the DD-WRT router configured and can access Internet.
Router Configuration Steps
- Connect a PC to the Lan port of the Router
- Using your browser, login to the admin page of Router B. By default this is available at http://192.168.1.1
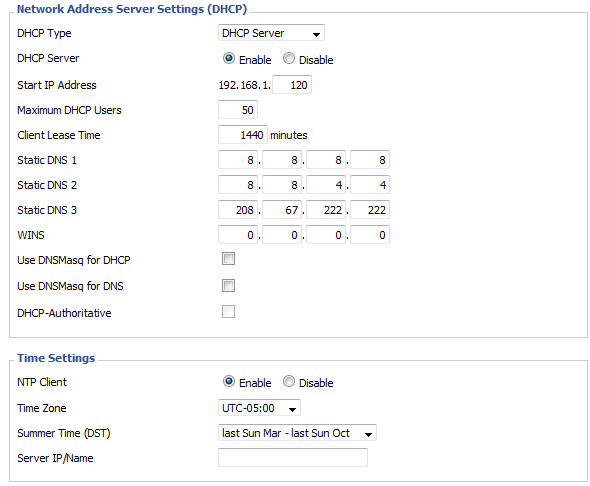
- Go to Setup > Basic Settings tab and set values as per below. Set the Static DNS to either OpenDNS or Google DNS. Uncheck / disable DNSMasq and DHCP-Authoritative checkboxes. Also set the correct date and time.
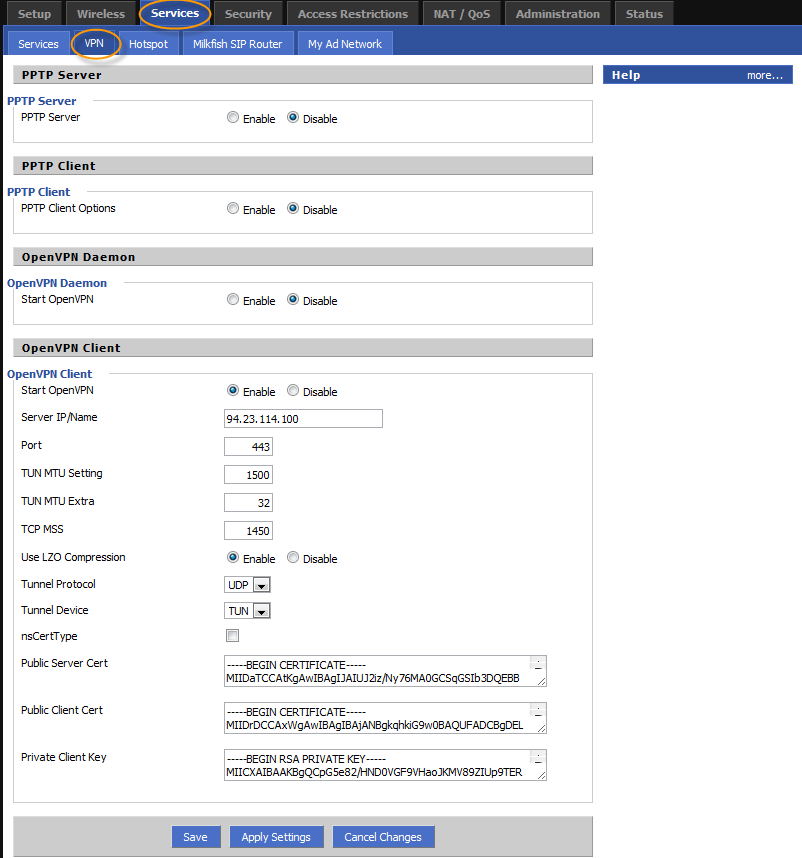
- Go to Services > VPN tab and set values as per below
- Start OpenVPN: Enable
- Server IP / Name: vpn.acevpn.com
- Port: 443
- Use LZO Compression: Enable
- Tunnel Protocol: UDP
- nsCertType: Checked
- Hit the Save button
OpenVPN Client
It would look like below screenshot when above steps are completed
- Go to Administration > Commands tab and set values as per below
- Paste the below content into "Commands" textbox, replace the USERNAME and PASSWORD with the credentials you received from Ace VPN and hit Save Startup button
sleep 30
echo "USERNAME
PASSWORD" > /tmp/openvpncl/userpass.conf
sleep 30
echo "client
dev tun
proto udp
hand-window 60
remote-random
#NOTE: Get additional IP's from the configuration file
remote 94.23.114.100 443
remote 76.73.56.41 443
resolv-retry infinite
nobind
persist-key
persist-tun
ns-cert-type server
comp-lzo
verb 3
keepalive 20 800
reneg-sec 0<ca>
-----BEGIN CERTIFICATE-----
MIIDaTCCAtKgAwIBAgIJAIUJ2iz/Ny76MA0GCSqGSIb3DQEBBQUAMIGAMQswCQYD
VQQGEwJBVjETMBEGA1UECBMKQWNlVlBOLmNvbTETMBEGA1UEBxMKQWNlVlBOLmNv
bTEQMA4GA1UEChMHQWNlIFZQTjESMBAGA1UEAxMJYWNldnBuLWNhMSEwHwYJKoZI
hvcNAQkBFhJtZUBteWhvc3QubXlkb21haW4wHhcNMDkwNTMxMjI0NDQ1WhcNMTkw
NTI5MjI0NDQ1WjCBgDELMAkGA1UEBhMCQVYxEzARBgNVBAgTCkFjZVZQTi5jb20x
EzARBgNVBAcTCkFjZVZQTi5jb20xEDAOBgNVBAoTB0FjZSBWUE4xEjAQBgNVBAMT
CWFjZXZwbi1jYTEhMB8GCSqGSIb3DQEJARYSbWVAbXlob3N0Lm15ZG9tYWluMIGf
MA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC1OxjeiDtjzNdlPTpbVpbXPDRY3OjL
Yuo/OSo2TfMkyYKloEzZtS8y9Cq4nhL63AkcZGh4rO6mQUOsQuse8203rt86Pcr2
MgTRWUh1sfqMWf+RwjwreosvK5G5xmp4U73IRmWgLCIMPYY+8JIHs3ztN0Dql6uX
rRGy+4kliydQswIDAQABo4HoMIHlMB0GA1UdDgQWBBRoNk+NYsacAC1J63np2h8U
9uTMCTCBtQYDVR0jBIGtMIGqgBRoNk+NYsacAC1J63np2h8U9uTMCaGBhqSBgzCB
gDELMAkGA1UEBhMCQVYxEzARBgNVBAgTCkFjZVZQTi5jb20xEzARBgNVBAcTCkFj
ZVZQTi5jb20xEDAOBgNVBAoTB0FjZSBWUE4xEjAQBgNVBAMTCWFjZXZwbi1jYTEh
MB8GCSqGSIb3DQEJARYSbWVAbXlob3N0Lm15ZG9tYWluggkAhQnaLP83LvowDAYD
VR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAAOBgQAorpiZ5LNXeMLxNv3/Ws2Fj8io
0TFmpxxF6wgK4vOXcpg/ypHALdb6nkSvooyHgzqe6mrAEmNKzb+/F7tPwtV/sI/b
mjpBgSpDnDtfd0YV/EiQh2nFzCi4MXSNThzMSF22iGm3QpXVEntTCY1aLBpO7C5C
jD/eoHK3Ok6tmxyyUQ==
-----END CERTIFICATE-----
</ca><cert>
-----BEGIN CERTIFICATE-----
MIIDrTCCAxagAwIBAgIBAzANBgkqhkiG9w0BAQUFADCBgDELMAkGA1UEBhMCQVYx
EzARBgNVBAgTCkFjZVZQTi5jb20xEzARBgNVBAcTCkFjZVZQTi5jb20xEDAOBgNV
BAoTB0FjZSBWUE4xEjAQBgNVBAMTCWFjZXZwbi1jYTEhMB8GCSqGSIb3DQEJARYS
bWVAbXlob3N0Lm15ZG9tYWluMB4XDTA5MDYwMzExNTEzNVoXDTE5MDYwMTExNTEz
NVowfTELMAkGA1UEBhMCQVYxEzARBgNVBAgTCkFjZVZQTi5jb20xEzARBgNVBAcT
CkFjZVZQTi5jb20xEDAOBgNVBAoTB0FjZSBWUE4xDzANBgNVBAMTBnN0YXRpYzEh
MB8GCSqGSIb3DQEJARYSbWVAbXlob3N0Lm15ZG9tYWluMIGfMA0GCSqGSIb3DQEB
AQUAA4GNADCBiQKBgQC3OvxRJCk6eCIF9UnmdlYuhkQ0s3+iDPggp2zfX+WQt61u
D3DWFx3Iy7vHkzS89hMVcuD94dB19xkhZPKdb+oO/lsiWraZSNAOo6lz91Ozypzk
oGLzyUqtGa6ySgGKJ73LHZBx/9/fltriLFhOBiGW6ZA79MmLnoRuJ1ND/6jBAwID
AQABo4IBNzCCATMwCQYDVR0TBAIwADAtBglghkgBhvhCAQ0EIBYeRWFzeS1SU0Eg
R2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBSbL59zGNLAej0cCr1AMco7
qLLiNjCBtQYDVR0jBIGtMIGqgBRoNk+NYsacAC1J63np2h8U9uTMCaGBhqSBgzCB
gDELMAkGA1UEBhMCQVYxEzARBgNVBAgTCkFjZVZQTi5jb20xEzARBgNVBAcTCkFj
ZVZQTi5jb20xEDAOBgNVBAoTB0FjZSBWUE4xEjAQBgNVBAMTCWFjZXZwbi1jYTEh
MB8GCSqGSIb3DQEJARYSbWVAbXlob3N0Lm15ZG9tYWluggkAhQnaLP83LvowEwYD
VR0lBAwwCgYIKwYBBQUHAwIwCwYDVR0PBAQDAgeAMA0GCSqGSIb3DQEBBQUAA4GB
AJ4SquZWulx7xEqm271QFy+3DH8okC2J9/EvOQ8+mGof7bTNDm9HjgI+AqqeE3k4
+g/0IsKdxOzLLNsrVfj4iuwK33cUHZnFRjIwFMtCO7RDokS2vxTCUcyS0T/7oKY/
Zydw0uR2laKtjzR2ldC+hKBEHuzQc0ppaeVRiEPNlUVw
-----END CERTIFICATE-----
</cert><key>
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQC3OvxRJCk6eCIF9UnmdlYuhkQ0s3+iDPggp2zfX+WQt61uD3DW
Fx3Iy7vHkzS89hMVcuD94dB19xkhZPKdb+oO/lsiWraZSNAOo6lz91OzypzkoGLz
yUqtGa6ySgGKJ73LHZBx/9/fltriLFhOBiGW6ZA79MmLnoRuJ1ND/6jBAwIDAQAB
AoGAUAFpeuSXO/iIoqFgC0lQiDAISBq4eEHBdkCkwURWMMKC77O+STz+vFZ5P8N/
G6M24f6vTyvyog+q4XH6ndPoFraksK4cFH56yBRxWcA9GbBt8gKauUmnOgHok9Ph
F3dzBTpSe7jVTman0ex8iyurEam2slyRmGAPjmrXD/dBmIECQQDgzWMGG9bxPaoY
daN74K/WJb0dBeib6aa5KL28KtWJmfiJgARbpCLTA4Dtj1AjeRBscyPPkCFM5n57
miLxpb4pAkEA0Kipw2vbzCnFz+UtSssG+6AkJP53kGzNCmdF0Nqu9YCtLAGhkgu4
yxXs6HzGRl5nh0XsY09qBInW0KzLVLUTSwJBALKa2/MNiV+Ps6XNST9xy6Jjx3XY
rO+62qi/ssdebNvvheSQ3mWE6donLXcQ5wXX+PGBJVGS3LJBavp/AwZkvckCQQCt
9iBrFA6RHbaVCD4FoFU3DiF0Uk9+sqcT6Fv1r4y0k85M5SM+btVnQ+VbQ0PPQT/R
MQPPHFOIax8UpSt0eO8XAkBkWRMZAa/+48QNNsJGoJKULkofUOgIoklQv3Yal7y1
y6rOqnFADqVE20Fg64Jx9xXiCxeoubn9twNpM5GG/16v
-----END RSA PRIVATE KEY-----
</key>auth-user-pass /tmp/openvpncl/userpass.conf" > /tmp/openvpncl/myopenvpn.conf
# The following line should be a single line with no line break
( sleep 20 ; killall openvpn ; /usr/sbin/openvpn --config /tmp/openvpncl/myopenvpn.conf --auth-user-pass /tmp/openvpncl/userpass.conf --route-up /tmp/openvpncl/route-up.sh --down /tmp/openvpncl/route-down.sh --daemon ) & - Now paste the below content into "Commands" textbox and hit Save Firewall button
iptables -I FORWARD -i br0 -o tun0 -j ACCEPT
iptables -I FORWARD -i tun0 -o br0 -j ACCEPT
iptables -I INPUT -i tun0 -j REJECT
iptables -t nat -A POSTROUTING -o tun0 -j MASQUERADE
Now reboot your router and wait for a minute for the router to establish a secure tunnel with Ace VPN gateway. Point your web browser at http://www.acevpn.com/, and scroll down a ways. In the border on the right you’ll see a box made of dotted lines, with an IP address, Hostname, city, etc. If AceVPN is working, the IP address, Hostname, City, State, etc. should all be something *other* than your own.
Troubleshooting
Refer DD-WRT troubleshooting steps.
Disconnects
If you’re unable to connect to the VPN server or can occasionally but not for more than a few minutes at a time, and you use a WAN device that does PPPoE onboard (Like a SpeedStream 5100b DSL Modem) — You may have to disable the onboard PPPoE and use the PPPoE on the WRT54G. The GRE that’s needed for the VPN sometimes gets messed up by your WAN device, probably because it uses a buggy layer 3 stack that corrupts or doesn’t pass the GRE packets to your WRT.
You may also have disconnects if the actual network that the client is on is the same subnet that the server is on (e.g. client subnet is 192.168.1.0/24 and the VPN server subnet is 192.168.1.0/24). This causes IP collisions. The best solution is to change the subnet of your client network to something unique, such as 192.168.5.0/24 (i.e. an IP range of 192.168.5.1-255 with a netmask of 255.255.255.0).
Enable logging
If you need assistance please email us the log. To enable openvpn log …
Add the following after “verb 3” in your startup script.
log /tmp/acevpn.log
Reboot your router, wait for about 5 minutes and then SSH / Telnet to your router and run the following command.
ln -s /tmp/acevpn.log /tmp/www/acevpnlog.html
Now go to http://192.168.1.1/user/acevpnlog.html and email us the contents of this page.
Enable syslog
To enable logging please follow the instructions at http://www.dd-wrt.com/wiki/index.php/Logging_with_DD-WRT